
QTC: Infrastructure of Blockchain 3.0 WEB3
BTC: Blockchain 1.0, Distributed Value
BTC is a decentralized monetary system. For the first time, BTC’s blockchain technology has introduced a consensus mechanism in a distributed database: Proof of work, which encourages participants to become participating nodes by rewarding native bitcoins to ensure consistent ledgers. BTC is a ledger that anyone can participate in bookkeeping, but no one can own this ledger in combination, so no one can change the records on this ledger. For the first time, a de-distributed currency system has been realized through technical means. transfer value. You can conduct transactions or transfers with anyone in the world, you only need to know the BTC address of the other party, and you do not need to confirm the bank or even provide a residential address.
The consensus mechanism of POW solves the problem of trust and does not need to trust a certain person or institution (which will give them huge power). Everyone can participate in the BTC network and become nodes to keep accounts together. A node can keep accounts and obtain the consensus of the entire network only after calculating the mathematical problem of the encryption algorithm, ensuring that the same BTC will not be used twice. If someone wants to maliciously attack the network, for example, transfer 1,000 BTC to their own ledger, then 51% of the nodes in the network need to agree to complete the modification. Now the participation of BTC is more like an arms race, the barriers to joining the network are getting higher and higher, and it is even more difficult to master 51% of the nodes, which ensures the security of the network. Therefore, BTC, as a distributed value, is more and more recognized by more and more people and has achieved global consensus.
However, the development space of BTC is limited. If you want to develop applications on the BTC network, POW-based Bitcoin only gives developers two choices, fork or develop on the original code. Those who choose to fork need to spend a lot of money to keep the original code running, and the scripting language of BTC created in 2008 is too primitive and difficult; if you choose to develop on the BTC network, the network layer, consensus layer and application layer of BTC are all mixed. Together, and the simple scripting supported by BTC is basically only suitable for transactions, it is difficult to continue to develop other functions on it.
2. Ethereum: Blockchain 2.0, the explosion of applications
The smart contracts brought by Ethereum have opened up the development space of application scenarios, and the blockchain can be adopted by more mainstream people. The Ethereum Virtual Machine, the Ethereum Virtual Machine simulates the processing system of the complete hardware system function, through which the application program can be run, which is the smart contract we see. Developers only need to tell the smart contract what to do and how to do it through code, and the rest only needs to be executed by the smart contract itself. Smart contracts liberate the development space of the application layer, and developers can build various applications that can be used by users and enter the era of blockchain 2.0.
But Ethereum still faces balance issues, namely scalability, availability, and independence. The existing DAPPs of apps deployed on the EVM are essentially competing for the limited block space on the chain, and the scalable space is limited: it is necessary to deal with various types of EVMs and only general optimization can be done, but different Application scenarios have different requirements. For example, Defi needs to be confirmed quickly, but NFT applications require storage space, so Ethereum cannot be suitable for all application scenarios, and the availability ceiling is low: all DAPPs based on EVM need to rely on the underlying environment of Ethereum, because EVM is deployed on each node on the Ethereum network, if the DAPP needs to be modified, it is also limited whether it is compatible with the underlying Ethereum network. Once a smart contract is deployed, developers can basically rely on the contract to run autonomously.
EVM really opens up the application scene space supported by blockchain as the underlying technology. A system like Apple’s IOS gives developers the space to create, turning a mobile phone from a single communication tool into an intelligent tool that includes social interaction, entertainment, and work. As the bottom layer of smart contracts, Ethereum’s EVM also gives developers unlimited creative space, bringing the decentralized financial system Defi we are seeing now, NFT that provides confirmation of rights, and a decentralized game economy. body gamefi.
However, as these applications gain more and more traffic and users, such as the Axie Infinity game with 2 million daily active users, the Ethereum public chain, which processes about 15 transactions per second, is obviously unable to carry such a huge amount of traffic. At the same time, smart contract upgrades are also very difficult and difficult to modify, and applications using smart contracts cannot iterate quickly to provide a better user experience. At the same time, other public chains have also begun to form their own ecosystems. Users hold certain assets in each public chain, but transferring assets across chains still faces many inconveniences.
3. QTC: Blockchain 3.0, Infrastructure of WEB3
Contribution direction of technology development:
Do Web3.0 infrastructure services on the blockchain storage track to create an effective information aggregator.
Solved problem:
The Problem with Centralized Search Engines
Instead of harvesting people’s data without their permission (or forcing their consent to use the solution), a distributed search engine protects users’ privacy. As a result, searches can remain private without requiring service providers to track users and transmit their data to third-party advertisers.
At the same time, by using blockchain technology, the distributed search engine can provide users with a transparent, censorship-resistant experience, and anyone can use the solution without any restrictions.
Also, while distributed search engines collect some data — mostly information that helps developers improve performance (such as location, search time, language settings), this information is encrypted and kept in the community members (miners) who maintain the network or verifier) on the computer.
Another great feature of distributed search solutions is that they have no middlemen, which means more value for advertisers. Blockchain projects that connect advertisers and consumers often provide incentives for users to partner with businesses.
The problem of centralization of computing power:
Qitchain Network uses the hard disk storage space to break up the centralized computing power, thereby avoiding the occurrence of monopoly. Qitchain Network writes the result of each collision to the hard disk by means of pre-calculation, and reconstructs the calculation in this way. As long as the hard disk is large enough and loaded with enough “answers”, any cryptocurrency enthusiast can participate in the production process of the block, and there is no need to repeat a large number of calculations. The problem of centralization of computing power is solved by Qitchain Network by exchanging space for time.
The CPoC consensus used by Qitchain Network is a very decentralized consensus algorithm. Compared with the waste of resources caused by PoW, CPoC will open up a new era based on hard disk capacity proof. CPoC uses the hard disk as the main carrier of consensus, so that ordinary people can also participate in the consensus through their own computers, so that everyone can participate in the road of decentralized innovation.
Meta-asset centralization problem:
We define the original asset as the native asset that comes with the blockchain system, such as Bitcoin as BTC, Ethereum as ETH, etc.
The CPoC consensus mechanism of Qitchain Network is based on hard disk resources, and each participant has the opportunity to become a block producer, ensuring a high degree of decentralization and fairness.
Energy consumption issues:
During the consensus process of Qitchain Network, miners only need to briefly retrieve the existing data in the hard disk according to the network requirements, and the system remains idle for the remaining time. The consensus model ensures low power consumption of the system.
Incentive design problems of traditional PoC consensus blockchain system:
Qitchain Network uses a dual incentive method when designing incentives, which can be mined through conditional or unconditional methods to adjust the income of each participant. Qitchain Network adopts a conditional approach to ensure the continuous development of the chain and the introduction of new miners, in this way to maintain the long-term positive development of the community.
The overall plan of the project:
The ecological system construction plan of Qitchain Network can be summarized by “three cores and two radiation belts”, including core support Qitchain Network, core service Qit Search, core world Qit Metaverse, service radiation belt, and technology radiation belt. The overall construction is as follows shown.
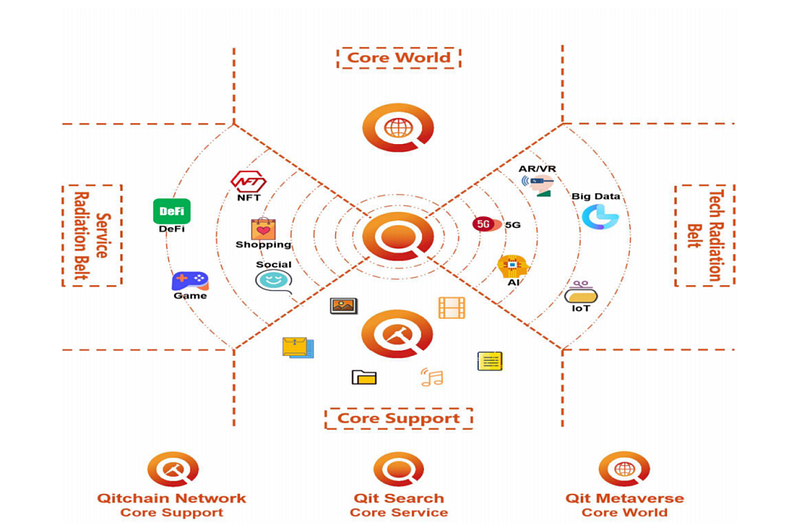
The future development plan of Qitchain Network will be divided into three stages, namely:
1) Phase 1: Effective Data and Network Security
Start efficient mining based on the CPoC consensus mechanism;
Design and implement standards for pooled mining protocols;
Maintain a stable group of miners;
Conduct proof-of-concept work for foundational services in the designed ecosystem.
2) The second stage: realize preliminary storage and retrieval
Improve Turing’s complete virtual machine, so that smart contracts can realize more functions;
Upgrade the CPoC consensus mechanism to CPoC+, and establish a perfect decentralized storage standard;
Establish a developer platform to allow more people to participate in ecological construction;
Complete the preliminary decentralized search engine to provide content services and information retrieval;
The service radiation belt forms a relatively complete system;
Started the tentative integration of the technology radiation belt with Qitchain Network and Qit Search.
3) The third stage: comprehensive ecological construction
Improve the decentralized search engine to achieve information aggregation, search-as-a-service and other capabilities;
The service radiation belt forms a complete service system;
Build Qit Metaverse based on Qitchain Network, Qit Search, and two radiation belts.
Current project development progress: Construction of the public chain
First of all, all applications that solve specific application scenarios need to be built on the underlying public chain. Specifically, the application layer that has the greatest impact on application development is the upper application layer of the public chain, and the network layer and consensus layer at the bottom of the public chain. It is the underlying performance of the application running, and the specific underlying design will not have more impact on the application itself as long as the performance is guaranteed.
However, if mainstream adoption is to be achieved, the entire public chain may be required to serve the application alone. For example, Axie, a popular chain game, chose to develop its own side chain Ronin to handle a large number of transactions. If you continue to rely on Ethereum, which carries other Defi, NFT and other transaction activities, it will not only be unable to handle the business of Axie games, but also cause congestion on the Ethereum network. After all, the TPS of Ethereum is only 10. Therefore, in the long run, a large number of applications piled up on a main chain to share resources cannot satisfy the application, but also drag down the entire network. It is impossible for a single public chain to be optimal for every application scenario. Projects on different tracks should choose to build on their own public chain ecology. At the same time, the explosion of applications on Ethereum also makes developers realize that different application scenarios have different requirements for the public chain. For example, the speed of confirmation time has a greater impact on the Gamefi project than the Defi project. Ideally, each application should have an independent blockchain, considering the large-scale usage scenarios in the future. However, it is neither necessary nor a waste of resources to develop the bottom layer of the public chain. At present, the design scheme of the public chain is basically the same, and the development workload is huge, and there are not many people who can actually do it.
The composition of the public chain: We can see what it takes to build a blockchain from scratch:
1. Data layer: Data storage technology, mainly based on cryptography data storage, to achieve transaction security, including Merkle tree, digital signature, hash function, asymmetric encryption technology, etc., store data in a block and then pass the chain The structure, combined with the technology of time stamps, is connected in sequence to form a block.
2. Network layer: The mechanism of node communication in the peer-to-peer peer-to-peer network, which affects the speed of information confirmation of the blockchain, and also determines the scalability of the blockchain.
3. Consensus layer: a unified accounting method, Let the decentralized nodes agree and confirm the records of the ledger to ensure the security of the blockchain.
4. Incentive layer: Encouraging nodes to participate in the blockchain through the economic incentive model, which is often referred to as the mining mechanism, is the basis for the operation of the blockchain 5. Contract layer: Smart contracts represented by Ethereum can be developed and automatically Execute the application 6. Application layer: user-facing product.
Qitchain’s network architecture:
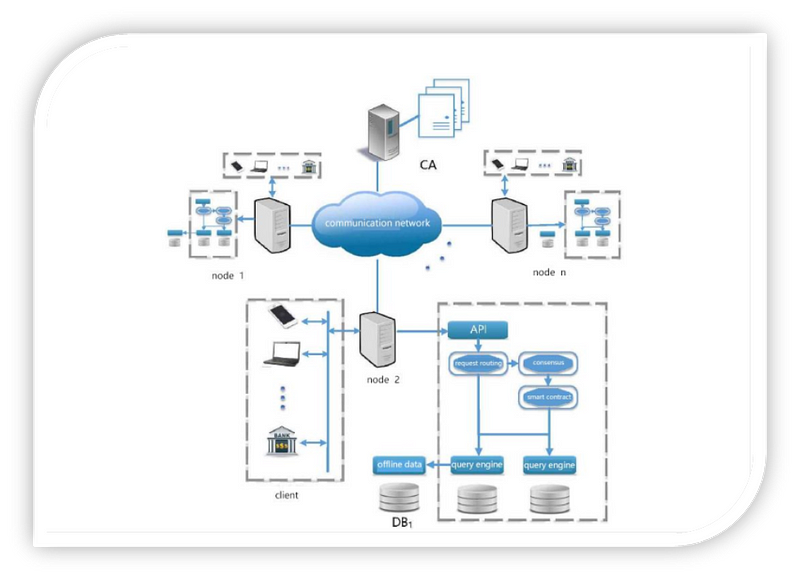
The system architecture of the QitChain system:
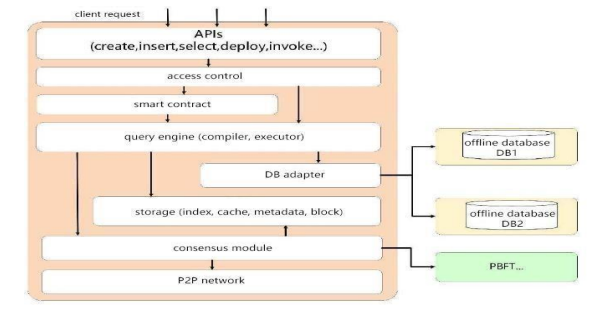
1. Application layer. The application layer has three modules: API, permission control and smart contract. The API provides a way to access the blockchain in SQL-like language; permission control verifies the request permission,
Qitchain protects user privacy through a multi-channel mechanism; smart contracts are used to create DAPPs (decentralized applications).
2, the query layer. The query layer receives the client’s query request, performs query analysis and query plan generation and execution, and returns the query result set to the client. The compiler is responsible for compiling the request into an internal representation, a parse tree, and the executor is responsible for generating and executing the query plan.
3. Storage layer. The storage layer is responsible for data structure maintenance and data storage, that is, index creation and maintenance, verification structure creation and maintenance, cache management, metadata maintenance, and block storage. In QITChain, the storage layer mainly includes four modules: cache module, index module, metadata module and block storage module.
4. Consensus layer. In order to ensure the consistency of block data between blockchain nodes, participants need to reach a consensus on the block data. The consensus layer ensures the consistency of data between nodes through a consensus protocol. Different consensus algorithms can be used in different application scenarios to Meet different needs.
5, the network layer. The network layer is responsible for message dissemination and data verification. QITChain adopts the Gossip protocol. The Gossip protocol is not only widely used in fault detection and member detection of distributed databases, but also in many blockchain systems to achieve block propagation and block data recovery.
The transaction execution process in Qitchain is as follows:
Users first deploy smart contracts or create blockchain lists on Qitchain through programming interfaces according to application requirements; then, for applications deployed using smart contracts, users can create table schemas for different transaction types to add relational semantics; after that, users send Transactions call smart contracts or insert data in the blockchain table to update the blockchain, and transactions sent by users will be packaged into blocks and consensus will be carried out according to the time period or transaction quantity threshold; finally, users can use SQL-like language to query block data .
Consensus Layer Design
Consensus service is used to ensure the consistency of block data between nodes. In Qitchain, the consensus module receives the transaction request sent by the client, packages it into a block and runs the consensus protocol to reach an agreement on the block data among multiple nodes. Different consensus protocols can be applied in different application scenarios. to meet different needs. In a public blockchain system, anyone can join the network, usually using a consensus protocol based on computing power, such as POW, which can prevent Sybil attacks. However, this method wastes a lot of computing power. In order to improve efficiency, part of the work has optimized POW and proposed new consensus protocols, such as DPOS. In the alliance chain, the number of nodes is limited and the participants are authenticated, so some systems use communication-based protocols such as PBFT as the consensus mechanism to improve the consensus performance. If it is assumed that the nodes in the system are not evil, non-Byzantine fault-tolerant consensus protocols such as RAFT or Paxos can be used to further improve performance. The CPoC consensus used by Qitchain Network is a very decentralized consensus algorithm. Compared with the waste of resources caused by PoW, CPoC will open up a new era based on hard disk capacity proof. CPoC uses the hard disk as the main carrier of consensus, so that ordinary people can also participate in the consensus through their own computers, so that everyone can participate in the road of decentralized innovation.
Nouns and concepts
Shabal: Shabal is the name of the encryption/hash function used in Qitchain Network. Shabal is a rather heavy and slow encryption compared to many other similar SHA256 algorithms. Hence, making it a good encryption scheme for proof-of-capacity for Qitchain Network. Because we store the precomputed hash while it’s still fast enough for small real-time verification. Qitchain Network uses the 256bit version of Shabal, also known as Shabal256.
Hash/Digest: A hash or digest is a Shabal256 encrypted 32Byte (256-bit) long string.
Nonce: When generating a Plot file, some bytes named nonces are generated. Each nonce contains 256 kilobytes of data that miners can use to calculate expiration dates. Each nonce has its own individual number. This number can range from 0 to 18446744073709551615. This number is also used as the seed when creating the nonce. Therefore, each nonce has its own unique dataset. A drawing file can contain many nonces.
Scoop: Each nonce is sorted into 4096 distinct data locations. These places are called scoop numbers. Each scoop contains 64 bytes of data, which contains 2 hashes. Each of these hashes is xored with the final hash (we get the final hash when generating the nonce).
Plotter ID: When a Plotter file is created, it will be tied to a specific BHD account. The Plotter ID will be used when creating random numbers. So all miners have different Plotter files even though they use the same nonce number.
Participate in the workflow of the network
1) Plot: The miner generates a Plot file on the local hard disk, fills the hard disk with the hash value containing its own public key, and integrates the Shabal algorithm. The larger the hard drive capacity, the more hash values are filled, and the higher the probability of winning the difficulty competition. The hash algorithm adopts Shabal256 algorithm, which has anti-ASIC characteristics.
2) Transfer: Transfer between wallets.
3) Forging: Miners monitor the P2P network, and each time a block is received, the packaging process of the next block begins. After a block is generated, the hash value of the block is sent to the miners, and the miners look for the most matching Nonce. After the wallet receives the Nonce, it converts the Nonce into a Deadline (time), and then waits for the end of this time to broadcast the block.
4) Verify: Verify after receiving the block.
Generate Nonce
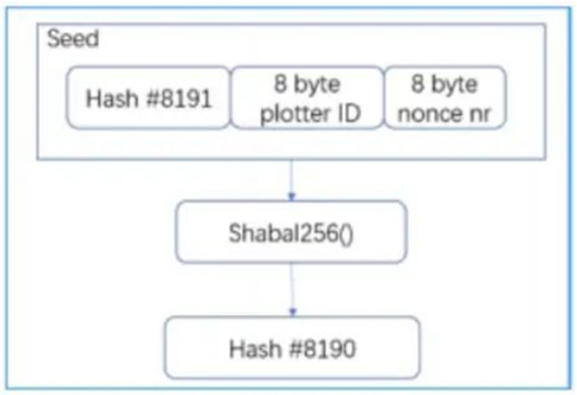
The first step in creating a nonce is to make the first seed. The seed is 16Bytes long, including Plotter ID and nonce number. Once done we generate the first hash with the Shabal256 function.
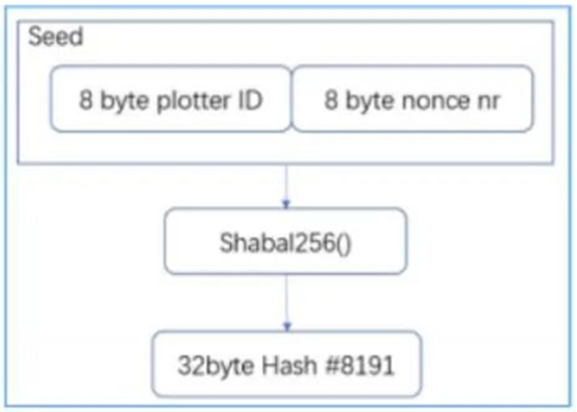
As the last hash in the nonce: #8191, append hash #8191 to the starting seed as the seed for the next round of Shabal256 computations.
Two hashes are created: hash #8191 and #8190. Append Hash#8190 to the last seed as a new seed.
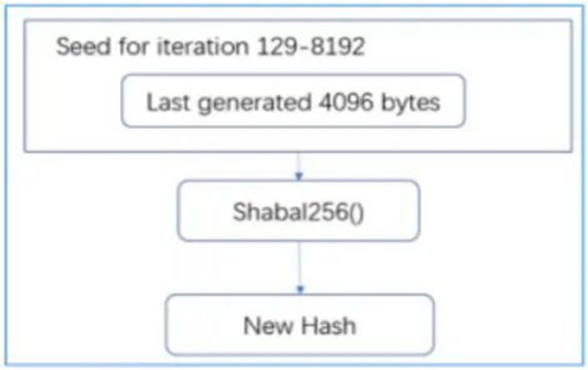
Create a new hash. For all 8192 hashes, continue appending hashes to, generating a new new seed. After 128 iterations, the seed length exceeds 4096 bytes. For the remaining iterations, only the last 4096 bytes are read.
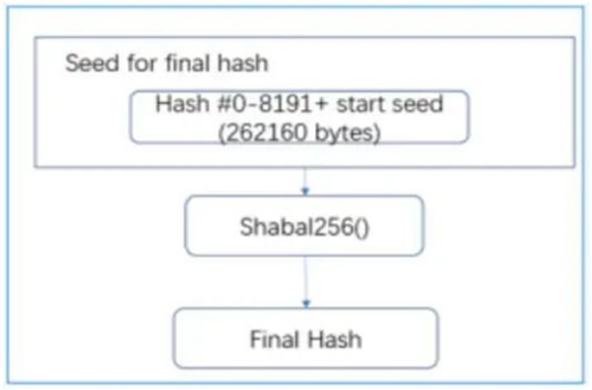
Generate the final hash (Final Hash), and use the generated 8192 hashes to create the final hash. All 8192 hash values and the first 16 bytes are used as seeds, and after the Shabal256 function is calculated, the final hash is generated.
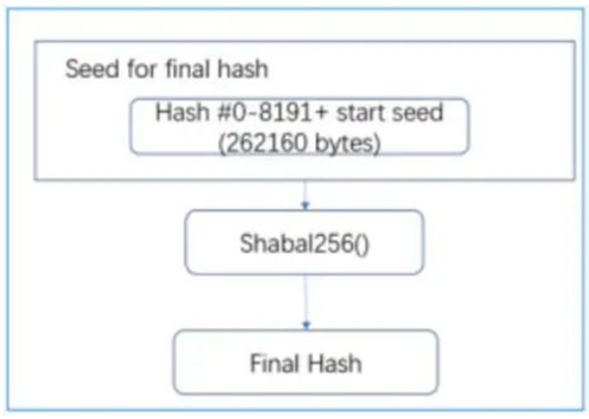
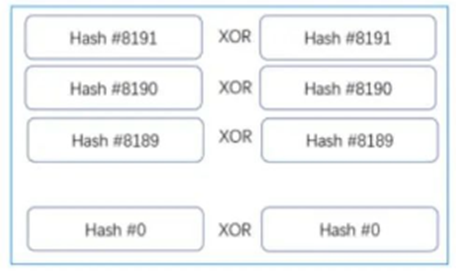
The final hash is exclusively XORed (XOR) all other hashes.
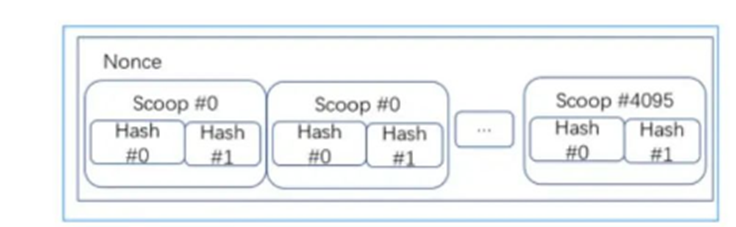
PoC format
In the process of POC construction, data shuffling needs to be performed at the end of the process. The process of data shuffling is as follows:
1) Divide the nonce into two halves, the first part is the nonce in the range 0–2047, and the second part is the nonce in the range 2048–4095;
2) The range 0–2047 is called low scoop, and the range 2048–4095 is called high scoop;
Take the second hash from the low scoop and swap it with the second hash from the mirror scoop in the high scoop range. The mirror scoop is calculated like this:
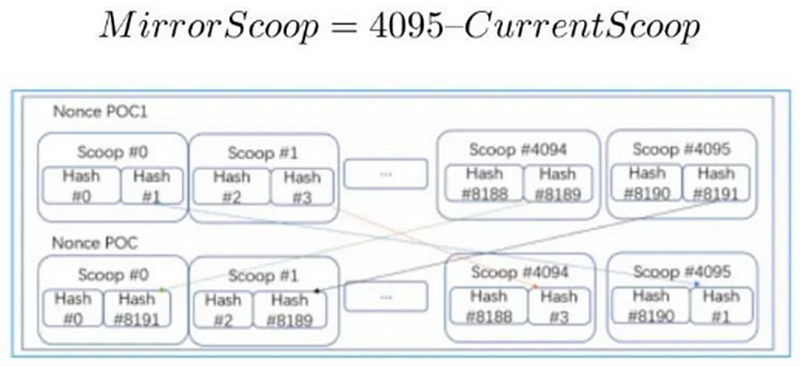
Plot structure
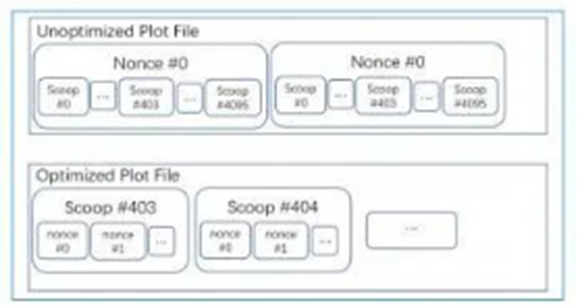
Read nonces from one or more plot files when participating in the network. The vendor software opens a plot file and looks for the scoop location to retrieve the scoop data.
If the plot file is not optimized, the scoop will be in multiple places. The example service provider below reads #403 scoop.
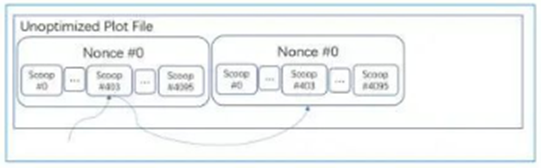
The service provider spends a lot of time searching for a location on the storage to read the scoop, which is very inefficient. To improve efficiency, the plot data format can be optimized. To this end, we have adopted the following optimization plan:
Reorder the data in the plot file to put the same scoop# data together. Divide the plot file into 4096 parts and split all nonce data according to the number of scoops. When the service provider wants to read Scoop 4096, it only seeks once and reads all data in sequence, which is more efficient and conforms to the linear read characteristics of mechanical hard disks.
CPoC consensus mechanism
Nouns and concepts: Shabal/Sha256: Shabal/Sha256 is a cryptographic hash function used in Qitchain Network. Shabal is a fairly heavy and slow cryptographic hash function, related to many other functions like SHA256. Therefore, it was able to become the encryption algorithm of Qitchain Network. This is because we store a precomputed hash and it’s still fast enough for small real-time verifications.
Deadline: When the calculation is started and the Plot file is processed, a value called deadline is eventually generated. These values represent the number of seconds that must elapse since the last block was forged before a block is allowed to be forged. If no one else has forged a block within that time, you can forge a block and get a block reward.
Block reward: If the service provider is lucky enough to mine a block, he will receive QTC as a reward. This is called the block reward. The block reward is reduced by 50% after every 568288 blocks.
Base Target: The Base Target is calculated based on the latest 288 blocks, and this value adjusts the difficulty of the service provider. The lower the benchmark target, the harder it is for service providers to find a deadline with a small value. The purpose of its adjustment is to try to keep the average interval between blocks as 3 minutes.
Network Difficulty: NetDiff for short, is a positive value, which can be regarded as an evaluation of the storage space of Qitchain Network. The unit is Byte. This value changes with the block and is based on Base Target.
Block height: Each block has a separate numerical number, each newly generated block will have +1 on the number of the previous block, this number is called the block height and is used to identify a unique block.
Generate signature: The generated signature is calculated based on the Merkle root and block height of the previous block. The service provider uses this value to generate a new block. The length of the generated signature is 32 bytes.
Block legitimacy check
As one of the distributed systems, the blockchain also has the problem that the distributed system does not have a unique global clock. In the Qitchain network, different service providers broadcast blocks with different deadlines to different nodes, and the current clocks of different nodes cannot be completely consistent. Therefore, nodes need a mechanism to deal with the legality check of synchronized blocks.
The BTC system adopts the method of setting a timestamp in each block to form a logical “clock”. Everyone recognizes this “clock” instead of their own clock, which has achieved a very stable and safe effect in practice. Therefore, Qitchain Network also inherited this solution.
In the Qitchain network, whether the block is successfully on the chain is directly related to the calculated deadline, and the process of verifying the legitimacy of the block can be expressed as:

The system directly compares the deadline of the current block with the timestamp difference between the current block and the predecessor block. Only when the deadline is less than the timestamp difference is a valid block.
Deadline legality check
During the drawing process of the service provider, two nonce files can be completely determined by the two parameters of nonce id and account id. Therefore, miners do not need to send a Nonce file with a size of 256KB to the node. They only need to send the block content and these two parameters to the wallet node when participating in the block generation. The wallet can calculate the entire Nonce value. After each node of the network receives each block, it will calculate whether its deadline is legal by calculating this Nonce.
Since the process of drawing by the service provider does not need to communicate and interact with other network nodes, this means that less interaction, simpler protocols and higher reliability are required in a large-scale distributed system such as a blockchain system.
Fork choice
In a blockchain system with PoW consensus, the logic for handling forks is very simple, and all honest nodes should consider the longest chain in the current network to be the main chain. However, the mining process of Qitchain does not require intensive CPU operations like PoW consensus. Service providers can often complete the traversal of the disk within 30 seconds, and the calculated deadline is the real control over the block time. Therefore, the main chain’s Judgment cannot be based solely on the longest chain.
In Burst, the indicator that reflects the amount of hard disk space is how many effective deadlines are accumulated. Among all competitors whose block height increases by one, the service provider that produces a block with a smaller deadline will probabilistically use more storage space and thus obtain the right to produce a block. Based on this point, the concept of difficulty accumulation is introduced into the Qitchain network, and the calculation method of difficulty accumulation can be expressed as:
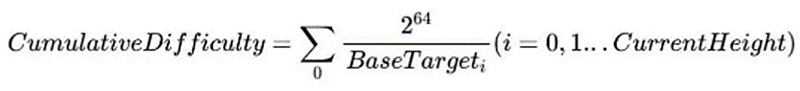
The index of difficulty accumulation intuitively reflects the amount of storage resources used on the current chain, so that honest nodes can choose the chain with the largest accumulated difficulty value.
Participant
Participants in the Qitchain network can be divided into six roles, namely pools, storage service providers, holders, wallets, exchanges and hardware service providers.

