
QTC, A RISING STAR IN PRIVACY COINS
Privacy and privacy protection form the cornerstone of the modern economy. This is especially true for blockchain technology, which was born at the beginning of Bitcoin.
Has an anonymous feature. So far, well-known privacy projects such as Monero, ZEC, and DASH have emerged. The independent public chain QTC has also announced the addition of zero-knowledge proof privacy technology to empower ecological upgrades.
1. The principle and logic of privacy coins
Take Bitcoin transactions as an example.
There are several elements that are essential when a payment is made to a recipient to conduct a transaction. These elements include the IP address of the payer, the amount of bitcoin paid, and the address of the recipient. As a participant in the blockchain, this information can be beneficial. For example, through the change of IP address, it is possible to roughly guess the flow of Bitcoin, and thus analyze the future trend of Bitcoin.
But as the counterparty, whether it is the payer or the receiver, such data exposure brings another side. The reason is very simple. The private data of the counterparty is exposed to the public. What’s more, the exposure of IP addresses may attract hackers, unidentified asset occupiers, and even personal safety.
This provides opportunities for privacy coins represented by Monero. Through specific processing technology, the privacy project successfully hides key data such as IP addresses, transaction paths, and transaction quantities for transaction users, so that the privacy of both parties to the transaction is well protected. As a result, privacy coins have gained the favor of transaction users and ushered in more and more crowds.
2. The transaction mechanism and mining mechanism of privacy coins
The core principle of privacy coins is to encrypt and transmit data through technical means, and ultimately achieve the purpose of effectively protecting user privacy data.
Monero shows us exactly what it takes to be a privacy coin: transaction anonymity, complete decentralization, and homogeneity. In the mining mechanism, although Monero also adopts a PoW mechanism similar to Bitcoin, the encryption mechanism is different, using the CryptoNight hash algorithm which is different from the SHA256 hash algorithm, which can only be used for CPU mining. It perfectly explains what is anti-centralization or decentralization.
In the initiation link, the payer successfully initiates a payment through the ring signature technology. The outside only knows that someone in the “group” of the ABC group initiated the payment, but it is impossible to know who initiated the payment.
In the transaction process, the trader hides the core information of the transaction through ring signatures and other methods.
In the acceptance stage, since each transaction will randomly generate a new recipient address that can be discarded after use, the recipient’s IP address is strictly protected.
Even if the same recipient accepts multiple payments, since different recipient addresses are displayed, the outside world has no way of knowing the recipient’s real IP address.
Due to the full encryption and protection of the entire transaction process, Monero was quickly welcomed by the market. According to Monero’s official website, from April 2020 to April 2021, the total transaction volume of Monero for the year reached 5,868,096, with an average daily transaction volume of 16,076. From April 2021 to April 2022, the total number of transactions rose to 9,087,482, a year-on-year increase of 54.86%; the average daily transaction volume was 23,542, showing a strong upward trend.
3. QTC and zero-knowledge proof, a rising star on the privacy track
QTC’s development path for private data is different from Monero and more similar to Zcash. There are very few teams that can run and apply zero-knowledge proofs in the world. Currently, both Ethereum and Litecoin are discussing the use of zero-knowledge proofs for privacy protection.
What is a zero-knowledge proof? As a simple example, if I pick up a cell phone with a passcode lock, you tell me that the cell phone is yours. At this point, if I want to verify the authenticity of your speech, I have two methods. The first method, use the password you know to open the phone. If the phone is opened, your authenticity is proven; if it is not, you will be falsified.
Compared with some other proof mechanisms, the advantage of zero-knowledge proof is that a trust mechanism can be quickly established between the prover and the prover, but the prover does not need to reveal the exact secret or thing to the other party. details to protect privacy.
QitChain, which is compatible with both the CPOC mechanism and the POS mechanism, fully absorbs the advantages of zero-knowledge proof and space-time proof, and provides a privacy protection solution for user privacy data protection. In the QTC ecosystem, you will see an anonymous voting mechanism, a highly confidential metaverse world, and other scenarios with high reliability but high privacy.
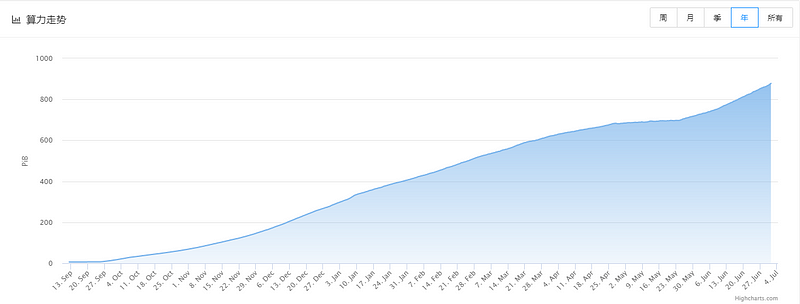
According to QitChain official website data, QTC’s computing power has shown steady and rapid growth since its launch. Up to now, QTC’s computing power has reached more than 900 PiB.
Armed with “zero-knowledge proof”, QTC has broad application prospects.
With the advent of the Web 3.0 era, the role of high-performance, scalable privacy coins and privacy chains for privacy protection will be further strengthened.
How convenient is the ecological industry processed through the “zero-knowledge proof” mechanism? Here is a simple example of transaction data.
In the financial system, many sensitive information such as deposit amount, home address, amount, password, etc., are easily leaked during the use process, and depositors’ funds are stolen or the deposit number of depositors is tampered with, which eventually leads to depositors. Damage to the interests of.
Through the data protection system of blockchain technology, only simple identification and legality verification are required, and through the asset encryption transmission mechanism, privacy and data elements can be protected while completing the settlement. In other words, the platform system only knows that the customer has transaction behavior, but has no way of knowing the details of the user’s specific data, etc.
Another typical case is securities trading. In securities acquisition cases, inside information supervision is a very difficult problem for regulators. The main reason is that it is difficult to identify and monitor the scope of insiders during the transmission of inside information, which leads to insider trading. This problem will be solved in the future through “zero-knowledge proof” technology. Within the framework of blockchain technology, who should know the relevant information, who knows how much information, and who is the insider of what information will be strictly authorized and kept confidential. This mechanism will greatly reduce the possibility of leaking insider information.
Of course, as a pioneer of Web 3.0, QTC’s technical development in privacy information protection is far more than that. In addition to the above cases, QTC will aim to build a Web 3.0 information aggregator, extensively develop “zero technology proof” protocols related to industrial ecology, and empower the government around the core features of anonymity, homogeneity and complete decentralization, science and technology, medical care, education, metaverse, technology application and other fields, play a protective role in supply chain finance, government bill logistics, insurance and other data on-chain.
